How to develop a security-first strategy for the cloud

Many organizations allocate their already-limited security resources to areas that don’t meaningfully deliver improved cloud security outcomes. Successful cloud security relies on a different mix of security controls than on premises. But the good news is that “Get back to basics” nicely sums up what organizations need to do to stay secure in the cloud. The new recipe for success stems from fundamentals of security such as asset inventory, configuration management and logging across services.
Bell and IDC partnered to survey 300+ medium and large organizations in Canada. The results reveal how varying approaches compare when it comes to preventing breaches. The lessons learned offer a great starting point for developing a security-first cloud strategy that will keep your data and workloads safer.
The state of cloud security in Canada
Based on the survey results, Bell and IDC identified four types of organizations that we have labelled as denialists, traditionalists, pragmatists and strategists. These groups differ in their degree of cloud adoption and effectiveness of their cybersecurity.
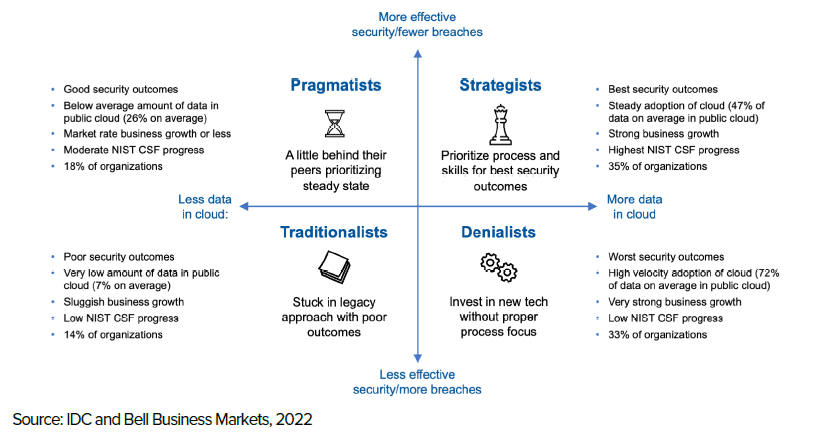
The Cloud security effectiveness matrix
- The s have the least effective security and are among the most aggressive adopters of the cloud. We can learn from them about key pitfalls to avoid. While they do invest in cloud security solutions, they fail to execute well on foundational elements of cloud security such as tracking configuration drift across their cloud assets. They do have some promising areas as they ‘shift left’ – they automate security controls early in the development pipeline. But, the security operations team needs to catch up with developers’ cloud-native capabilities to monitor and secure more APIs, a broader software supply chain and many new applications in production.
- Unlike the denialists, the traditionalists are held back by layers of legacy technologies. Like the denialists, their security effectiveness is below average. This is because of the amount of technical debt they’re mired in and a lack of security resources to protect their organizations.
- The pragmatists are moving to the cloud at a slower-than-average rate, but seem to be taking many of the right actions to achieve improved cloud security. They ensure their security staff receive training to augment their traditional security skills with the new ways of defending against attackers gaining initial access in the cloud, for example. A cautionary note about these organizations is that they’re missing out on inherent security benefits of cloud adoption such as easier integration and orchestration for better threat detection and response across cloud services.
- Finally, the strategists show above-average cloud adoption and the most effective cloud security. This group exemplifies which actions tend to result in improved security. They have a well-rounded approach to cybersecurity that focuses on continuously mapping their inventory of cloud services, APIs and access rights. With this foundation, they can identify misconfigurations and perform better logging and monitoring for early threat detection
Both the strategists and denialists have invested heavily in the cloud, moving more data there than other organizations, and both have seen success in terms of business growth. Where they differ is in their security outcomes, with the strategists experiencing the fewest breaches and the denialists the most.
What accounts for this stark difference? The denialists have taken a cloud-native approach to application development but don’t have the accompanying security operations capabilities to function at a higher throughput of code nor in a different style of architecture. They focus too heavily on technology, while the strategists understand that training people and solid processes are also critical to staying protected in the cloud.
It’s worth mentioning that the strategists also tend to take advantage of stronger integration and automation capabilities in the cloud, which leads to better security than is typically possible in on-premises IT. This also helps explain their security edge over the other groups who have been slower to adopt the security advantage of the cloud.
Three elements of successful cloud security leadership
By comparing the cloud security actions of the successful strategists and the struggling denialists, three key principles emerge, all of which must be acted upon continuously. These three principles closely align with the Identify and Detect functions of the NIST Cybersecurity Framework.
1. Take inventory of your cloud services
Although easier said than done, get to know your ever-changing cloud attack surface by identifying all the cloud services (and their dependencies) your business is using. It is foundational to effective security, but so often organizations fail to do this well. You need to be aware not only of the cloud services employees are using, but also how those services are accessed and what data is stored in them. Identifying the inventory of cloud services goes beyond cloud access security brokers’ (CASB) discovery capabilities to also include continuous attack surface management (ASM) and software composition analysis (SCA)). Together, these solutions map out the obvious and less obvious exposures you may have across a multicloud reality.
Furthermore, consider your software supply chain — every component, library, and package that comprise each individual cloud service is at risk. This recipe of so ftware components/vulnerabilities (known as a software bill of materials SBOM) needs your attention. Software composition analyses can help you document each dependency and the associated vulnerabilities.
2. Focus on proper configurations
According to Gartner, 99% of security breaches in the cloud are due to misconfigurations – often caused by human error. Misconfigurations can inadvertently expose data, credentials or open APIs to potential attackers. Examples of misconfigurations include exposed storage access, unencrypted databases, disabled logging, dormant accounts left open and so on. The chance of a configuration error is even greater if you use multiple clouds because configuration options and security settings are not consistent from service to service.
Preventing misconfigurations requires constant assessment of settings and expertise with cloud services, APIs, code, containers and templates. While the skills to do this can be hard to come by, especially amid Canada’s ongoing tech talent shortage, there are tools and managed services that can alert you to possible misconfigurations and recommend actions to remediate them. Solutions such as cloud security posture management (CSPM) and SaaS security posture management (SSPM) help find and notify you of configuration issues.
3. Log and monitor
The importance of a well-defined inventory of services, applications, APIs, identities and data described in step 1 above is essential for good threat detection. You need to detect and contain a breach as quickly as possible – and cloud logs are central to early detection. Doing so requires continuous monitoring across your cloud services to flag early signs of malicious activity and attempts at initial access wherever it may occur. Focus on critical areas of cloud intrusion detection such as unauthorized access and abuse of credentials. Also, the typical telemetry used in on-premises detection and triage apply in the cloud.
To make the best use of your resources and ensure the right security events receive attention, you should also have processes in place to triage alerts and orchestrate response through automated playbooks across cloud assets. Thankfully, cloud services are typically rich with access to log data from APIs for this purpose.
Fundamentals matter
At the core of executing on a cloud security strategy are tools known as cloud-native application protection platform (CNAPP), which provide continuous monitoring of cloud configurations, entitlements and workloads. They can show visually how well your organization is progressing towards meeting its objectives within a range of cybersecurity frameworks.
Ultimately, the success of any cloud security strategy depends on a balance across people, process and technology. Strength in any one area will only get you so far. To stay protected, you need to consider the whole picture and build your defences accordingly. Use CNAPP tools to see and fix the gaps.
While advanced cloud security practices like threat hunting are important, it’s critical to get “back to basics” by continuously taking inventory, managing configurations, and logging and monitoring across all your cloud services.
For proof, just look to the experiences of the hundreds of Canadian organizations that have either thrived or struggled in the cloud. By following the lessons learned from those that have seen success, you can develop an effective strategy that will keep your data, workloads and business safer.
How does your cloud security match up to your Canadian peers? Learn how Bell Cloud Security Solutions can help your business.